The frequency of cyber-attacks continues to increase at an unparalleled pace. By attacking the most vulnerable value chains of organizations, they result in information confidentiality & integrity breaches, discontinuity of business activities and huge financial and reputational damages. Once considered predominantly as a technological issue, the risks related to the information systems are now evaluated within the Enterprise Risk Management scope.
On the other hand, traditionally, Business Continuity Management (BCM) is mostly treated as a domain separate from Information System Security Management (ISSM). With the rapid explosion of cyber threats, the alignment between BCM and ISSM is now becoming a must, in order to provide management with a holistic view and enabling them to implement organizations where the teams closely interact with each other.
It goes without saying that the organizational part of security and BCM is the key for a successful implementation, yet the information system (IS) part needs to also be addressed in an efficient way. Various standards and frameworks exist to help organizations implementing a BCM, but they lack, on one hand, practical guidelines enabling a pragmatic and efficient implementation, and, on the other hand, a strong link with the governance, architecture and security of the IS.
In this article we will introduce very briefly an innovative approach and describe the first steps for the linkage of the ISO© 22301 Standard to the SABSA® Methodology for Enterprise Security Architecture and Strategy, enabling an efficient implementation of BC based on an architectured and secured IS.
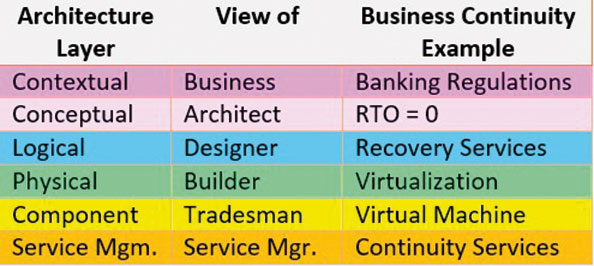
SABSA Layers (Quelle: ISACA)
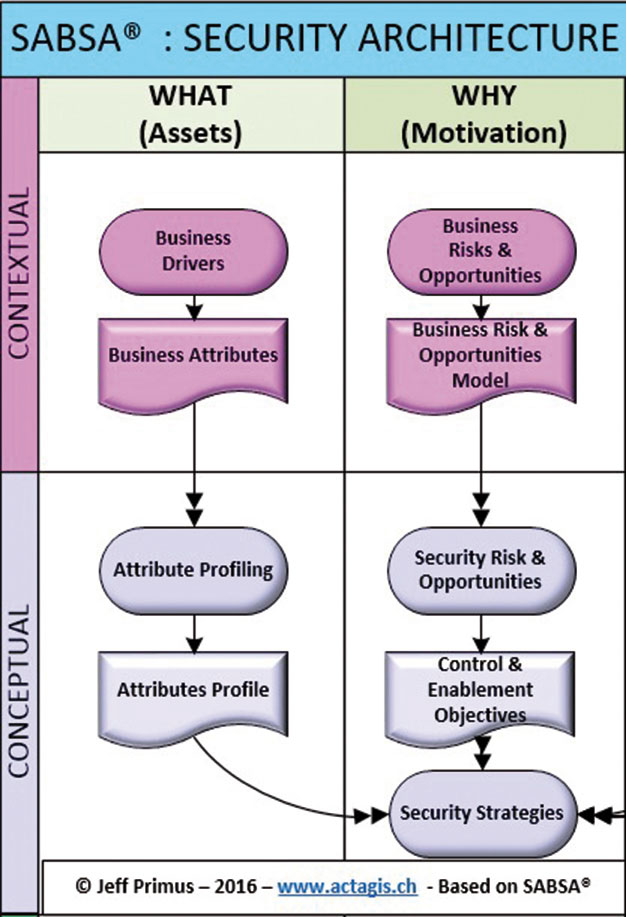
SABSA Security Architecture (Quelle: ISACA)
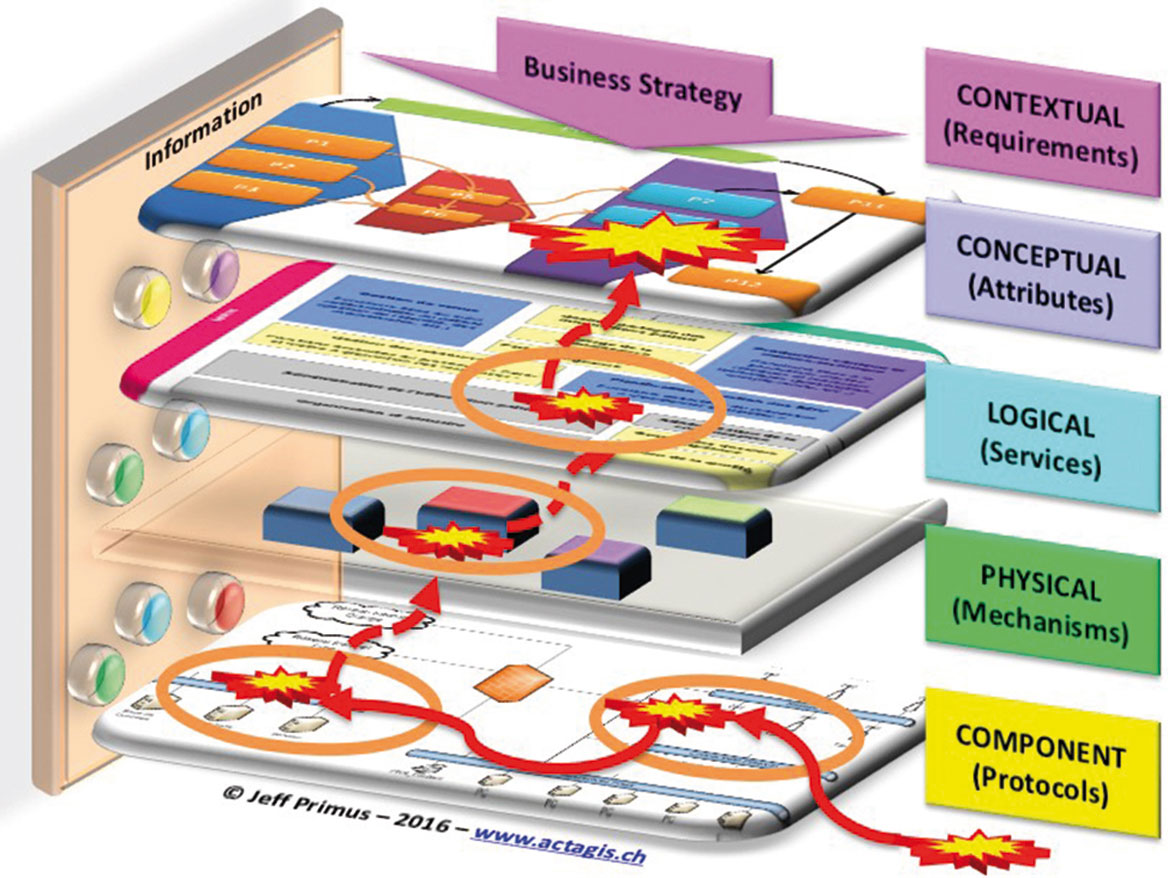
Cyber attack causing discontinuity (Quelle: ISACA)
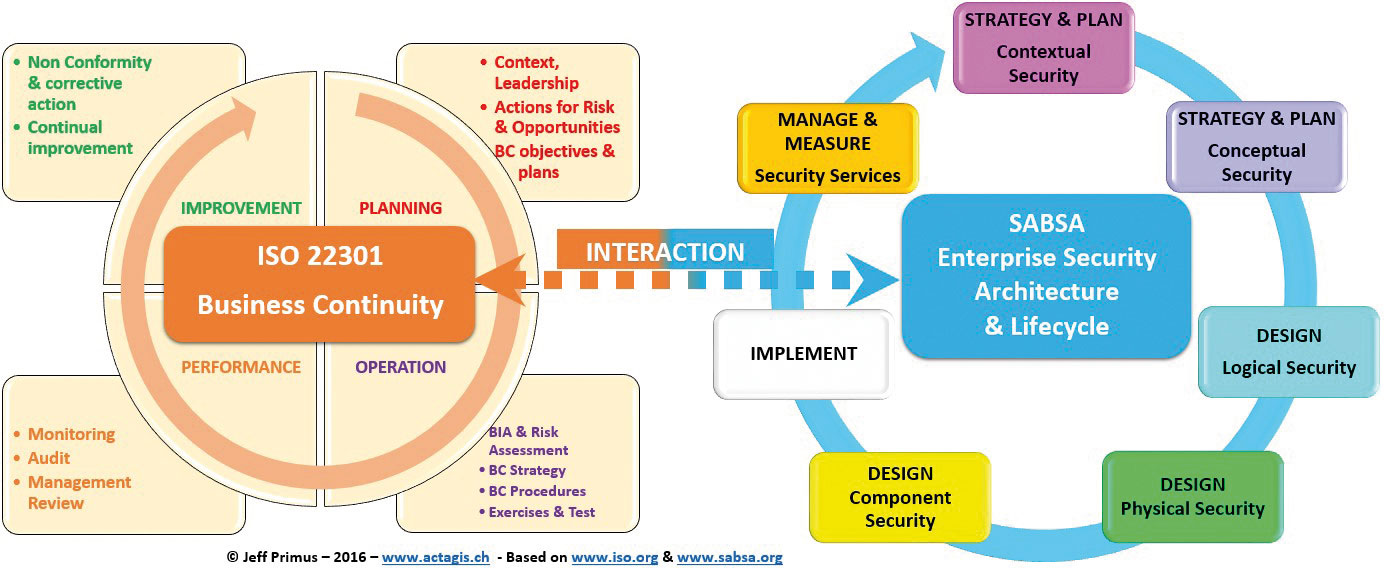
Interaction between ISO 22301 and SABSA (Quelle: ISACA)
ISO 22301 Standard
Business Continuity is defined as the capability of an organization to continue the delivery of products or services at acceptable predefined levels, following a disruptive incident. Based on this definition, BCM can be seen as a holistic management process. It identifies potential threats to an organization and their impacts to business operations. More importantly, it provides a framework for building organizational resilience, preparing an effective response that safeguards the interests of its key stakeholders, reputation, brand and value-creating activities. Within this context, ISO 22301 enables a BCM System (BCMS) that establishes, implements, operates, monitors, reviews, maintains and improves BC. The owner of BCM should be at the CEO level of the organization. BCM structures the following activities:
Planning – During the initial phase of the BCMS, management buy-in is obtained, the organization’s needs, strategic objectives, context and scope are determined, emphasizing the intention of the organization to address the risks & opportunities and to comply with the regulations. Next, empowering of key competences and provisioning of resources are initiated. Additionally, the document lifecycle and communication management, which are key for the success of BCM, are also put in place.
Operations – The major activities related to this phase are: Business Impact Analysis (BIA), Risk Assessment (RA), Strategies, Procedures, Exercises and Tests. For instance, during the BIA step, business requirements such as Recovery Time Objectives (RTO) are captured.
Performance Evaluation – In order to prepare the basis for the improvement phase, the BCMS should now be monitored to verify its effectiveness, efficiency and compliance with the BC objectives. Internal audits and management reviews are also periodically performed in order to analyze and evaluate the performance of the BCMS and identify possible nonconformities.
Improvement – This is the final phase of the cycle where the nonconformities are controlled and corrected using the appropriate actions.
SABSA: Enterprise Security Architecture
SABSA is a proven methodology for developing risk-driven enterprise information security and assurance architectures and enabling secured information systems that support critical business initiatives. Adopted worldwide by organizations of all sizes, it is an open standard, comprising a number of different stakeholders in the process of specifying, designing, constructing and using the business system.
At each layer, the six fundamental questions are answered: "What, Why, How, Who, Where and When". As an example we have shown below the high level answers to these questions "What" and "Why" applied to the Contextual (Business) and Conceptual (Architect) layers.
One of the strengths of SABSA is its attribute model enabling requirements engineering to span the full IS security lifecycle. Another crucial notion is "security domain Framework", where a security domain is defined as a set of elements subject to a common security policy. Among other SABSA elements, these two models, coupled with the risk management framework, enable the methodological construction of the building blocks for a secured and architectured information system.
The linkage between ISO 22301 and SABSA
As an example, the figure below shows how a cyber-attack can use the vulnerabilities of a given domain (surrounded by an orange colored ellipse) to find a way to attack another domain of the organization and hence causing by cascade a major discontinuity of the business activities. In order to avoid such situations, there are various possibilities to link ISO 22301 to SABSA. A straightforward way is to adopt SABSA’s attribute, risk, domain modeling.
During the planning phase of ISO 22301, the requirements and the expectations of the interested parties can be expressed via the SABSA attributes (at the Contextual and Conceptual layers).
During the operations phase of ISO 22301, the SABSA risk management framework (the WHY column of the schema at the left) enables the expression of the risks and opportunities via the attribute profiles. This then enables the creation of the security and various domain policies. Coupled with the outcome of the BIA, the security domains can now inherently integrate the continuity and security services that will protect the organization from various cyber-attacks.
By integrating SABSA to the Business Continuity Management System, your organization will be prepared for the new cyber era, in a holistic and cost effective way.
For further information about Business Continuity (ISO 22301, BCI), SABSA and
ISACA trainings, certifications and services you can contact us at www.actagis.ch
About the author
Jeff Primus, Founder & CEO of ACTAGIS
Official and Accredited
ISACA, BCI, PECB Trainer for ISO 22301 Lead Implementer, SABSA-SCF, AMBCI, CISA, CISSP, CGEIT, CRISC, COBIT5, ISO 27001 LA & LI, ISO 20000 LI, ISO 27005 Risk Manager (teaching in French and English).
He has over 25 years of experience within information systems governance, security and business continuity. Jeff, as an experienced manager, leads teams of consultants and actively participates in business critical missions. Jeff, as an expert of the subject, actively implements ISO 22301, SABSA and ISO 27001 compliant Business Continuity & Security Management Systems for the public sector and multinational companies in Switzerland, Europe and the Middle- East. As a lead lecturer, he teaches Security, Governance and Business Continuity topics at the University of Paris-Sorbonne and University of Geneva. Additionally he has written many articles on security and information systems and been featured on radio and television shows. Jeff is a board member of ISACA-Switzerland and Chapter Lead ISACA Suisse-Romande. He also took actively part in the ISO SC27 Workgroup, which co-defines the new releases of the ISO 27001 standard.